AWS Solution Architect Associate Exam Study Notes: VPC (Virtual Private Cloud)
- Oct 10, 2017
These notes were written while working through the A Cloud Guru AWS Certified Solutions Architect - Associate online course. These notes are partly from the videos, and also from various other online sources. Primarily, they’re notes for me, but you might find them useful too.
Since the AWS platform is changing so quickly, it’s possible that some of these notes may be out of date, so please take that into consideration if you are reading them.
Please let me know in the comments below if you have any corrections or updates which you’d like me to add.
This post was last updated in March, 2019.
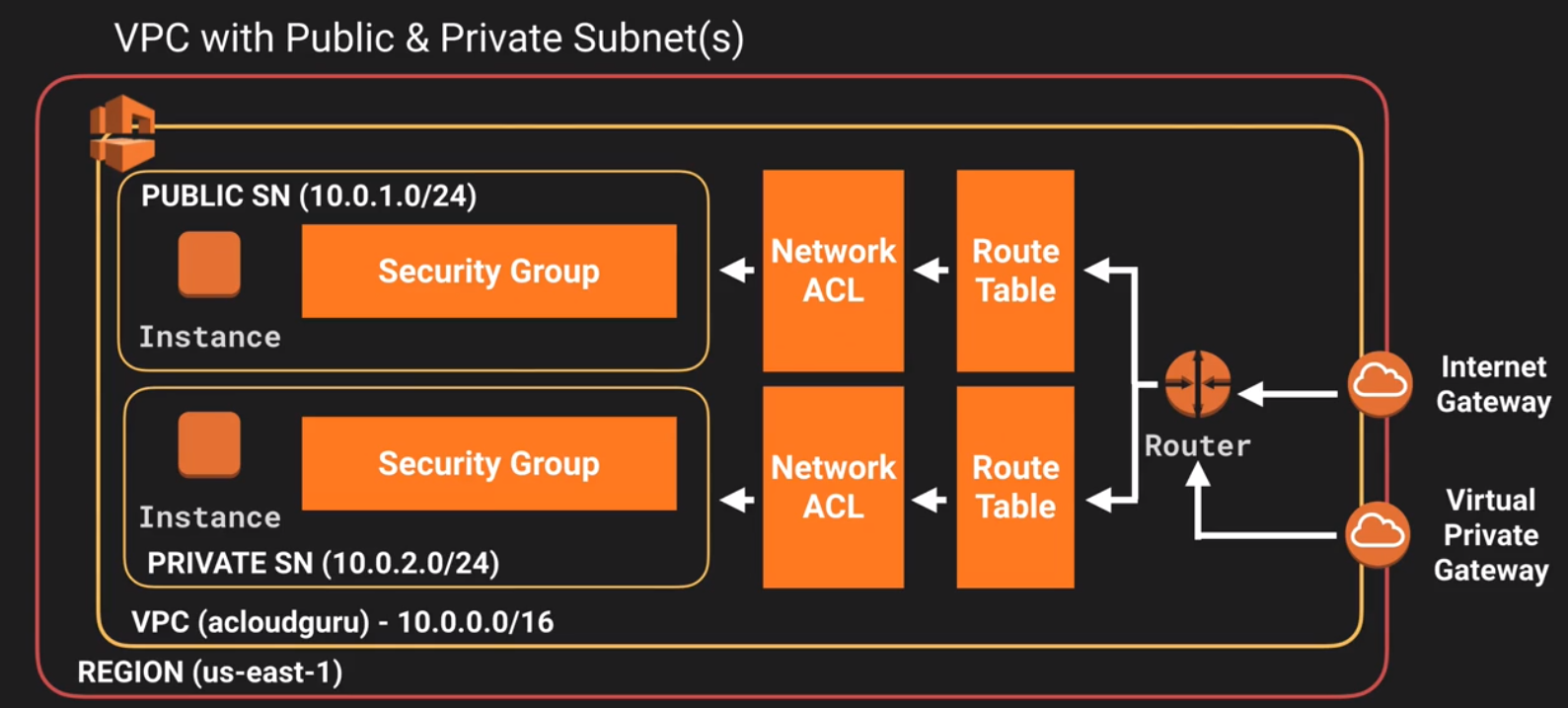
VPC (Virtual Private Cloud)
VPC applies to all exams. Need to know this inside-out.
A VPC is like a logical data center.
A VPC consists of:
- Internet Gateways or Virtual Private Gateways
- A VPC can have only one internet gateway
- Route Tables
- NACLs (Network Access Control lists)
- Security Groups
All VPC traffic can be logged via Flowlogs.
In an Amazon VPC, an EC2 instance retains it’s private IP address when the instance is stopped.
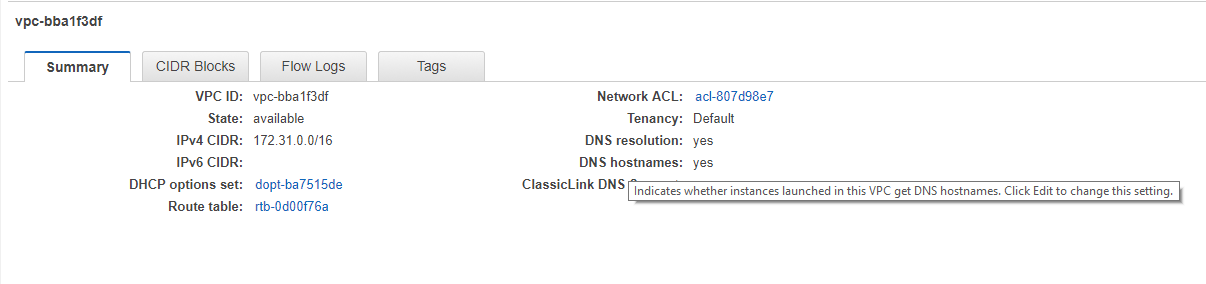
VPC DNS Names
If you want instances in a VPC subnet to get DNS hostnames, make sure you set DNS hostnames to “yes” in the VPC configuration:
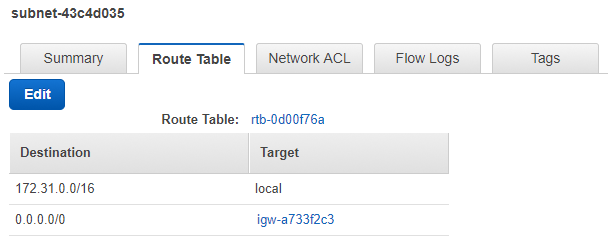
VPC Internet Gateway
Creating a VPC also creates a route table, but doesn’t create a subnet or internet gateway by default.
For a VPC route table point to an internet gateway, you must first attach the internet gateway to the VPC.
You can attach only one internet gateway to a VPC at a time; if youre getting an error when trying to attach an Internet Gateway to a VPC, it could be that an Internet Gateway is already attached to the VPC.
Before deleting an IGW, you must first detach it from the VPC it’s attached to.
More info on VPC Internet Gateways
VPC Virtual Private Gateway
An Amazon VPC VPN connection links your data center (or network) to your Amazon VPC virtual private cloud (VPC). A customer gateway is the anchor on your side of that connection. It can be a physical or software appliance. The anchor on the AWS side of the VPN connection is called a virtual private gateway.
VPC Subnets
- Use public facing subnets for public facing web servers
- Use private subnets for backend services, databases, etc.
Each subnet is always mapped to an AZ (Availability Zone); subnets are strongly bound to an AZ - it’s not possible to span subnets across multiple AZs. However, security groups, NACLs, and Route Tables CAN span multiple subnets and AZs. Remember: 1 subnet = 1 AZ
Only one internet gateway can be attached to a subnet.
How to access instances in a private subnet
You can use a Bastion / Jump Box located in the public subnet to access instances in the private subnet by:
- SSH into the Bastion
- and then using it to SSH to instances in the private subnet. i.e. via
ssh -i MyEC2KeyPair.pem [email protected]
Layers of security
For multiple layers of security, it’s recommended you use a VPC in addition to security groups and NACLs (Network Access Control Lists).
Security groups (first layer of defense) exist at the instance level.
NACLs (second layer of defense) exist at the subnet level.
It’s possible to implement a private cloud (i.e. a corporate data center) using VPCs.
CIDR - Classless Inter-domain Routing
The first four IP addresses and the last IP address in each subnet CIDR block are not available for you to use, and cannot be assigned to an instance.
i.e.
- 10.0.0.0: Network address.
- 10.0.0.1: Reserved by AWS for the VPC router.
- 10.0.0.2: Reserved by AWS for DNS.
- 10.0.0.3: Reserved by AWS for future use.
- 10.0.0.255: Network broadcast address. We do not support broadcast in a VPC, therefore we reserve this address.
Network masks:
- /16 - supports up to 65,536 IP addresses. Best for large networks.
- /24 - supports up to 256 IP addresses. Best for smaller networks.
- /27 - supports up to 32 IP addresses
- /28 - supports up to 16 IP addresses
- /32 - an absolute ip address - matches exactly one
It’s possible to split a CIDR block into two subnets:
- one subnet can use CIDR block 10.0.0.0/25 (for addresses 10.0.0.0 - 10.0.0.127)
- and then the other subnet can use the CIDR block 10.0.0.128/ 25 (for addresses 10.0.0.128 - 10.0.0.255)
The allowed CIDR block size in a VPC is between a /16 and /28 netmask.
To enable ping, you need to allow ICMP traffic.
In order to ensure providioned EC2 instances have a public IP address, enable “Auto-Assign Public IP” for the subnet.
Subnets and route tables
In order for instances in your subnet to be able to access the internet, ensure that there is appropriate an entry on the route table such as 0.0.0.0/0 -> Internet Gateway
i.e.
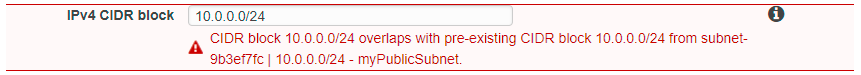
Subnets and CIDR blocks
Subnets in a VPC cannot have overlapping CIDR blocks:
Security groups vs NACLs
| Security Group | NACL |
|---|---|
| Supports only Allow rules | Supports Allow and Deny rules |
| Stateful | Stateless |
| All rules are evaluated before allowing traffic | Evaluates rules in numerical order. As soon as a rule is found allowing the traffic, the traffic is allowed. |
| Rules apply to specific instances | Rules apply to ALL instances in the subnet |
| Unable to block IP addresses | Able to block IP addresses |
A NACL can be applied to multiple subnets. If you attempt to assign a NACL to a subnet which already has a NACL, the new NACL will replace the existing NACL for the subnet.
A subnet can have only one NACL assigned to it
Types of NACL:
- Default - allows all traffic by default
- Custom - denies all traffic by default
In order to allow outgoing traffic, enable outgoing and incoming ephemeral ports (1024-65535)
NAT gateways and NAT instances
NAT is used for traffic routing
It’s best practice to always enable HTTP and HTTPs traffic.
Must be provisioned into a public subnet, and it must be part of the private subnet’s route table in order for your instances in the private subnet to communicate with the outside internet.
Instances within a private subnet cannot communicate with the outside internet by default. In order for your instances within the private subnet to communicate with the internet (i.e. to run “yum update”), you’ll need to add 0.0.0.0/0 with the target pointing to your NAT gateway/instance to the route table in the private subnet
| NAT instance | NAT Gateway |
|---|---|
| Custom EC2 instances provisioned via custom community AMIs | Provisioned and managed by AWS |
| The amount of traffic handled by a NAT instance depends on it's size - bigger instances handle more traffic. | Managed by AWS and scale automatically up to , and are prefererred over NAT instances which are custom community AMIs. |
| NAT instances use security groups | . |
| Need to disable source/dest checks disabled via the Actions->Networking menu. | No need to disable source/dest check, no security group is needed; it is all AWS managed, rather than a custom EC2 instance which needs to be maintained. |
| Must be in the public subnet and must have a public ip address. | . |
| Performance depends on the instance size/td> | Scale automatically up to 10GBPS |
NAT Gateways
When creating a NAT gateway you must specify the public subnet in which it should reside, and also specify the Elastic IP (EIP) address to associate with it.
After creating the NAT gateway, you then need to update the route tables associated with one omr more private subnets to point internet traffic to the NAT gateway.
If the NAT gateway gets created with a failed status, the NAT gateway will be visible for short period of time (usually an hour), then will be automatically deleted.
You cannot route traffic to a NAT gateway through a VPC peering connection, a VPN connection, or AWS Direct Connect. A NAT gateway cannot be used by resources on the other side of these connections.
Source/dest checks (applies to NAT instances only)
Source/dest checks are there to ensure that the EC2 instance by default must be the source or destination of any traffic it sends or received.
We want to route any outgoing traffic through our NAT instance, and route any traffic coming back in through our NAT instance. Because of this, we need to disable source/dest checks.
Here’s an example of a NAT instance community AMI:
Amazon provided NAT instances have the string amzn-ami-vpc in their names, so you can easily search for them in the console.
Full comparison between NAT gateways and NAT instances
AWS Managed VPN Connections
- Virtual Private Gateway - the VPN concentrator on the Amazon side of the VPN connection. You create a VPG and attach it to the VPC from which you want to create the VPN connection
- Customer Gateway - a physical device or software application on your side of the VPN connection.
To create a VPN connection, you must create a customer gateway resource in AWS, which provides information to AWS about your customer gateway device.
AWS supports Internet Protocol security (IPsec) VPN connections.
aws ec2 describe-vpn-connections --vpn-connection-ids vpn-1a2b3c4d
{
"VpnConnections": [
{
"VpnConnectionId": "vpn-1a2b3c4d",
...
"State": "available",
"VpnGatewayId": "vgw-11aa22bb",
"CustomerGatewayId": "cgw-ab12cd34",
"Type": "ipsec.1",
"Category": "VPN"
}
]
}
More info on AWS Managed VPN Connections
Stateful vs Stateless
Security groups are stateful. This means that if you add an incoming HTTP rule, there will automatically be a corresponding outgoing one.
Subnet ACLs are stateless which means that if you add an incoming HTTP rule, you’ll need to add an outgoing one too, otherwise HTTP traffic won’t be able to get back out of your subnet.
Default VPC
AWS provids a default VPC. This is intended to make it user friendly to deploy and test EC2 instances on a new account. All default VPCs have routes out to the internet.
If you delete the default VPC, you’ll need to raise an Amazon support ticket to get it back.
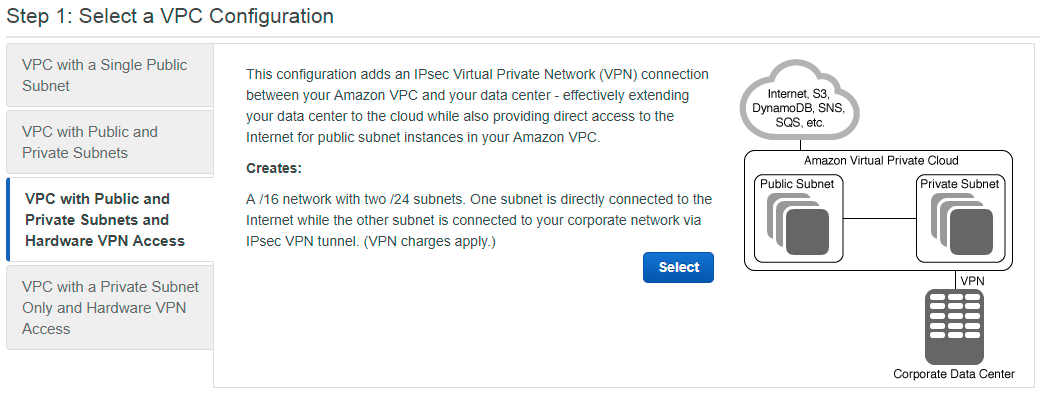
VPC Wizard Options
VPC Peering
VPC peering can be used when a VPC needs to communicate with another VPC.
VPC Peering is supported across multiple accounts.
VPC peering allows direct network connection via a private ip address. Instances behave as if they were on the same private network.
The following peering configurations are invalid:
- Overlapping CIDR blocks
- Transitive peering
- Edge to edge routing through a gateway or private connection
More info on invalid peering configurations
VPC peering is only supported in a star configuration.
Transitive peering / edge-to-edge routing is not supported. i.e. if you have VPC A <-> VPC B <-> VPC C, VPC A can communicate with VPC B, and VPC B with C, but A cannot directly communicate with C unless a direct connection is made between A and C.
You must update both sides of the route tables for VPC peering to work
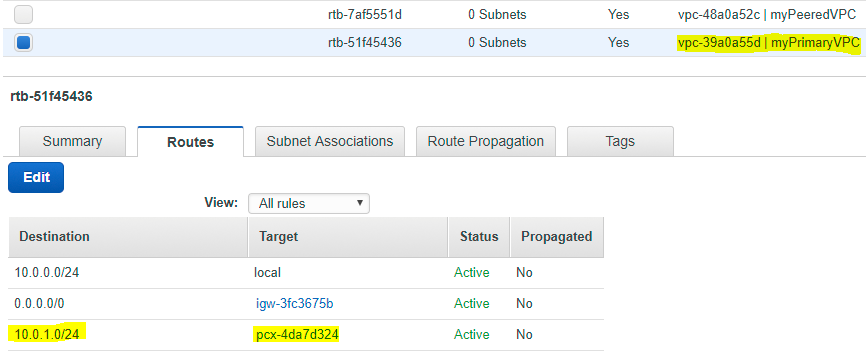
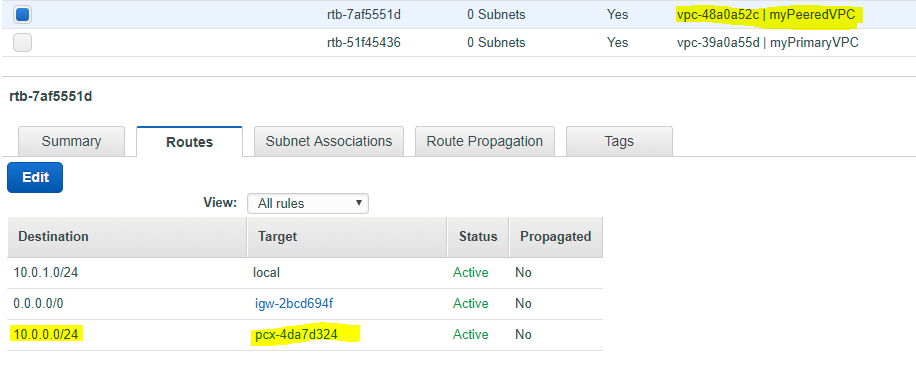
In the screenshots below, myPrimaryVPC and myPeeredVPC are peered, and have route tables which allow traffic to be routed between each other. If ICMP rules are enabled in security groups, they can ping each other.
myPrimaryVPC’s Route Table
myPeeredVPC’s route table
Direct Connect
Direct connect uses a dedicated line, provisioned by your telco, between your data center and an AWS Direct Connect Facility. Data transferred via direct connect does not travel over the internet.
While VPCs are quick to set up, direct connect can take more than a month, and sometimes more than 6 months to get set up.
Having a VPN connection is considered as a backup to a Direct Connect connection.
Elastic Network Interface (ENI)
Also referred to as a “Network Interface”, is a virtual network interface that you can attach to an EC2 instance in a VPC. Network interfaces are available only for instances running in a VPC.
You can attach a network interface to an instance:
- When it’s running (hot attach)
- When it’s stopped (warm attach)
- When the instance is being launched (cold attach)
Note that an Elastic Network Interface can only be reassigned within the same AZ, and cannot be assigned to an EC2 instance in a different AZ.
Exam tips
Know how to build out a VPC from memory before going into the exam. Even though you don’t actually build a VPC in the exam, the knowledge of how to build it out from memory will be immensely helpful.
Know the difference between:
- Public and private subnets
- NAT gateway and NAT instance
Know what a bastion host is, and that it is possible to use a dual purpose web server and bastion host.
Want to read more?
Check out the AWS Certified Solutions Architect Associate All-in-One Exam Guide on Amazon.com. The book getting great reviews, was updated to cover the new 2018 exam SAA-C01, and is available on Kindle and as a paperback book.
See my full exam tips here: AWS Solutions Architect Associate Exam Tips
And click here to see all of my notes: AWS Solutions Architect Associate Exam Notes
